|
In this article, I'll discuss how you can customize the terminal services client to create a custom build version.
You can customize your client and use it with the TSVer utility that came with the Windows 2000 Resource Kit. TSVer can restrict what client builds can connect to your terminal server.
Thus, if you use this tutorial to create a custom build of your client, you can restrict who can connect to your terminal server based on who you give your customized client to.
You can download TSVer here and get more information about utilizing TSVer here
Due to the scope of this article, I won't go into the nitty-gritty details about the disassembly of mstscax.dll or how I determined what hex address to change. If you have questions pertaining to the disassembly, please feel free to e-mail me.
If you are interested in disassembly, I would highly recommend W32DAsm. Extremely powerful disassembler and process debugger.
For this tutorial, I'm going to change a build 2600 RDP client into a build 2601. You can choose whatever number you'd like to change it into, just make the necessary changes as you see fit.
Prerequisites:
•The latest version of the RDP client, build 2600 or later
•Any hex editor that will tell you the current offset you are at in your file. I'm using Hacker's View (HIEW) in this article. It is shareware and will do the job just fine.
Step 1: Backup your main files
•After you have installed your client, make a backup copy of mstscax.dll. This is for good measure. It can be found in your %SystemRoot%\System32 directory.
Step 2: Check your mstscax.dll version
•Before we start hacking the mstscax.dll, we need to determine what version we are using.
•Find your mstscax.dll and right click on it, then click properties. Click on the version tab and check what the 'File Version' is. Most likely it is 5.1.2600.0 or something similar. See Figure 1, below, for a screenshot.
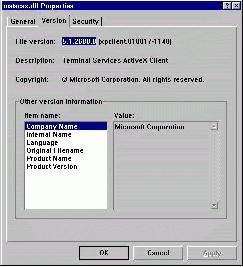
Figure 1. Mstscax.dll's version, 5.1.2600.0
Click the image for a larger version
•Make note of that version number. That number is the build number of the mstscax.dll, and a terminal server can detect that build number when you connect. Figure 2, shown below, is a screenshot of tsadmin.exe showing the client build of 2600.
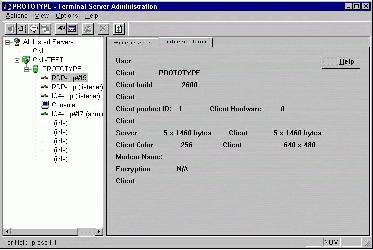
Figure 2. TSAdmin's view of the client's build.
Click the image for a larger version
Step 3: Patch the mstscax.dll
•Now that you know the build number, use Table 1, below, to determine what the Hex Address of where you are going to patch.
Table 1.
Client Build Number
|
Hex Address
|
Hex Offset
|
5.1.2600.0 (Windows XP version)
|
6A634EEF
|
0x000342EF
|
5.1.2600.1106 (Windows XP SP1 version)
|
6A640EB4
|
0x00040EB4
|
5.1.2600.2180 (Windows XP SP2 version)
|
6A646834
|
0x00045C34
|
5.2.3718.0 (Windows Server 2003 RC2 version)
|
605F0ACA
|
0x0003FECA
|
5.2.3790.0 (Windows Server 2003 version)
|
60110B42
|
0x0003FF42
|
5.2.3790.1433 (Windows Server 2003 SP1 RC2 version)
|
6A648F7B
|
0x00048375
|
5.2.3790.1830 (Windows Server 2003 SP1 version)
|
6A648F7B
|
0x00048375
|
•For this tutorial, we are going to be looking at address 6A634EE9 of the mstsacax.dll.
•Now, start up your hex editor and go to the hex address you just looked up (in this case, 6A634EEF). In HIEW, the hex editor I'm using, I hit Enter once, to switch into hex editing mode, then hit F5 to use the goto function.
I then typed in ".6A634EEF" (without the quotes). If the search properly executed, then you'll see a screen similar to Figure 3, shown below.
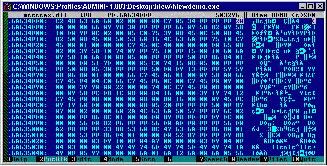
Figure 3. The unedited mstscax.dll.
Click the image for a larger version
•You'll notice at this point that the number 28 is highlighted. You'll also notice that the next number, located at 6A634EF0, is 0A. Just so you know, 0A28 is hex for 2600, which is the build number we are tying to hack.
•For this tutorial, I'm going to change the build from 2600 to 2601, so using my handy calculator, I determined that 2601 converted to hex is 0A29, which means I need to change the 28 to 29.
•Getting hack to HIEW, hit F3 to enter into editing mode, then change the 28, at hex address 6A634EEF, to 29. Hit F9 to save the changes, then hit F10 to exit HIEW. Figure 4, shown below, displays the end product.
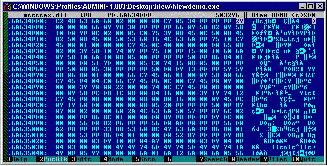
Figure 4. The edited mstscax.dll.
Click the image for a larger version
•Now, put the hacked mstscax.dll back into your %SystemRoot%\System32 directory and then startup mstsc.exe. Connect up to your terminal server, and then bring up tsadmin.exe. Figure 5, shown below, is what you should see. You'll notice that tsadmin now recognizes the client build as 2601, rather than 2600, which means that our hack has worked.
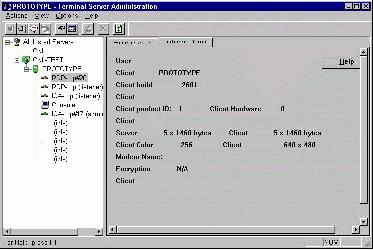
Figure 5. TSAdmin's view of the client's build.
Click the image for a larger version
Well, that's about it. You've just finished hacking the mstscax.dll.
And...no tutorial would be complete without a download, so here is the version I created (compressed):
 MSTSCAX.zip
MSTSCAX.zip
|